


IoT Smart-Locks: Apple HomeKit & Schlage Sense-lessness (or how to spend $2000 on a deadbolt)
The goal Upgrade home-office security and take the opportunity to join the Star Trek generation of smart-home IoT. Exec summary Describe my experience installing and configuring a couple of Schlage Sense smart-locks and configuring them to connect to a couple of Apple...
Highlights from the Apple Worldwide Developers Conference 2016 (WWDC16)
Apple held WWDC16 in San Francisco earlier this month to introduce new versions of iOS, tvOS, watchOS, and a new version of OS X that’s been rebranded as macOS. These new versions are available to developers now and will be more widely available through Apple’s Public Beta program soon, with final releases this Fall. Alongside the new software, Apple announced some exciting changes coming to the App Store, too: Search Ads and more open and flexible subscriptions.
Learning Auto Layout for iOS, tvOS, and OS X
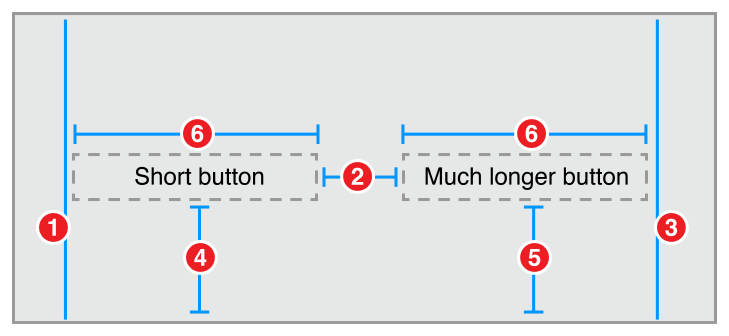
With the release of the iPhone SE and the iPad Pro, along with the expectation that iPad apps will include support for slide over and split screen mode it’s now clear that Auto Layout is here to stay. If you’re not already developing apps using Auto Layout and Size Classes now is a great time to learn more about them and prepare yourself for any updates to the APIs that Apple introduces at WWDC in June.
Fortunately there’s a lot of great resources to quickly get up to speed and learn the best way to support a variety of devices and size classes in your next app.
